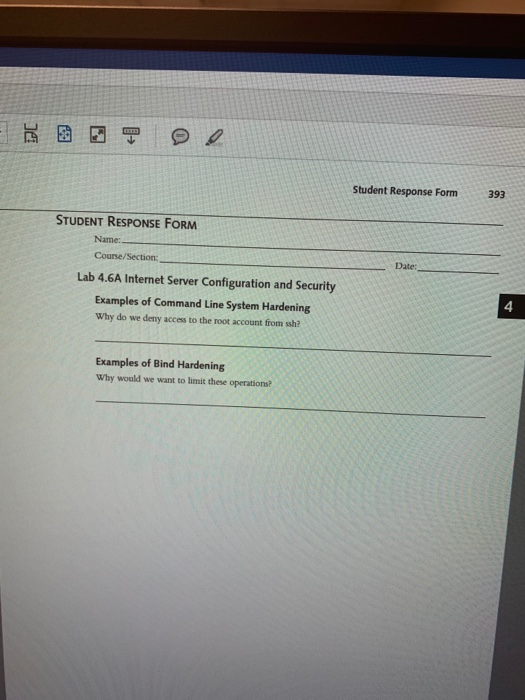
 393 Student Response Form STUDENT RESPONSE FORM Date Lab 4.6A Internet Server Configuration and Security Examples of Command Line System Hardening Why do we deny access to the root account from ssh? 4 Examples of Bind Hardening Why would we want to limit these operations? Show transcribed image text 393 Student Response Form STUDENT RESPONSE FORM Date Lab 4.6A Internet Server Configuration and Security Examples of Command Line System Hardening Why do we deny access to the root account from
393 Student Response Form STUDENT RESPONSE FORM Date Lab 4.6A Internet Server Configuration and Security Examples of Command Line System Hardening Why do we deny access to the root account from ssh? 4 Examples of Bind Hardening Why would we want to limit these operations? Show transcribed image text 393 Student Response Form STUDENT RESPONSE FORM Date Lab 4.6A Internet Server Configuration and Security Examples of Command Line System Hardening Why do we deny access to the root account from
OR
OR
