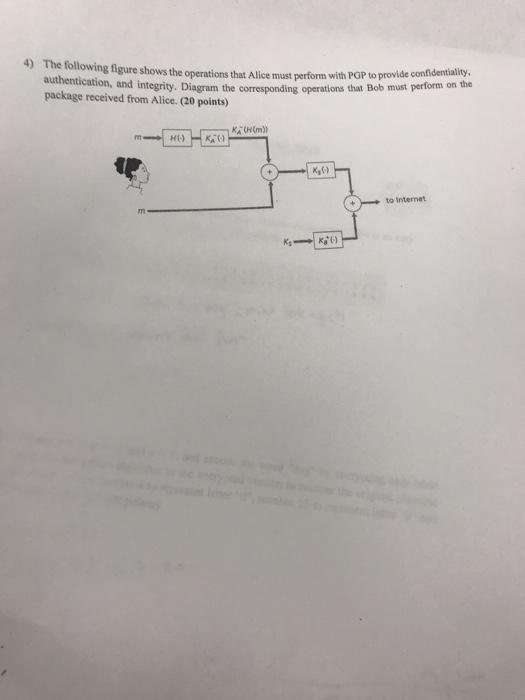
 4) The following figure shows the operations that Alice must perform with PG authentication, and integrity. Diagram the corresponding operations that package received from Alice. (20 points) P to provide confidentiality, Bob must perform on the Ks() to Internet Show transcribed image text 4) The following figure shows the operations that Alice must perform with PG authentication, and integrity. Diagram the corresponding operations that package received from Alice. (20 points) P to provide confidentiality, Bob must perform on the
4) The following figure shows the operations that Alice must perform with PG authentication, and integrity. Diagram the corresponding operations that package received from Alice. (20 points) P to provide confidentiality, Bob must perform on the Ks() to Internet Show transcribed image text 4) The following figure shows the operations that Alice must perform with PG authentication, and integrity. Diagram the corresponding operations that package received from Alice. (20 points) P to provide confidentiality, Bob must perform on the
OR
OR
