The log file should be runed for live capture for the detectionof the attacks , can be found by installing secure onion andfinding it from Intrusion detection file.
Example of a log file runed in Security onion, virtual box foranalyzing the detection.
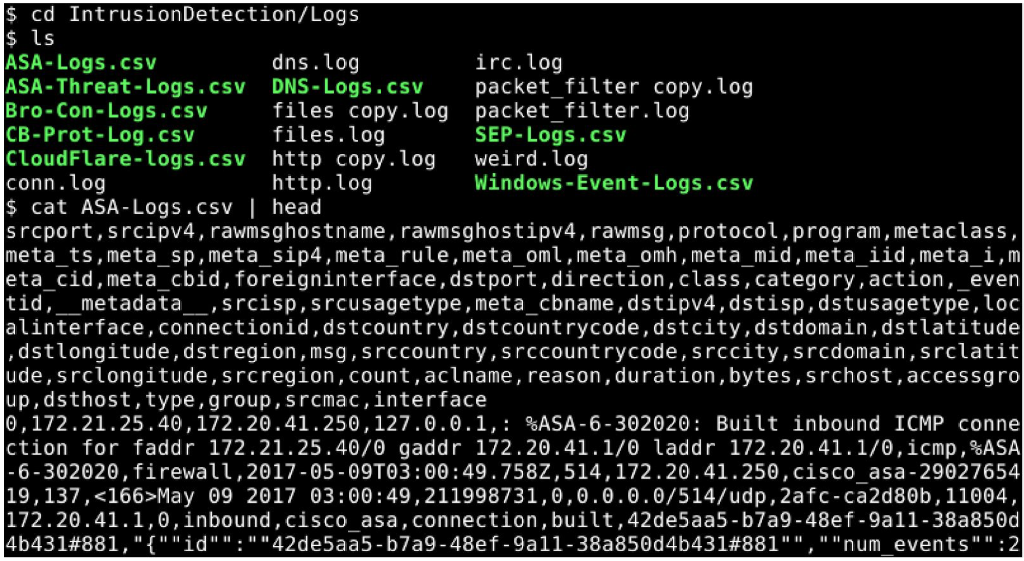
We were unable to transcribe this image$ cd IntrusionDetection/Logs dns.log irc.log ASA-Logs.csv ASA-Threat-Logs.csv DNS-Logs. csv Bro-Con-Logs.csv CB-Prot-Log. csv CloudFlare-logs.csv http copy.log weird.log
OR
OR
