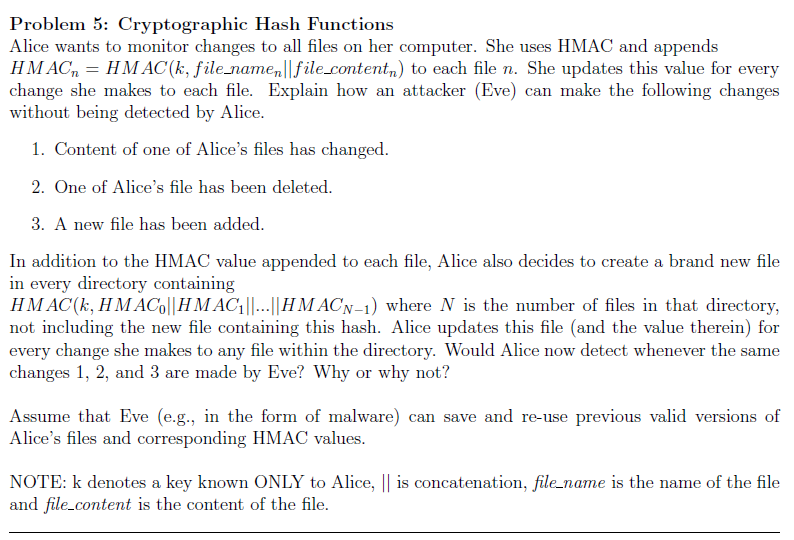
Problem 5: Cryptographic Hash Functions Alice wants to monitor changes to all files on her computer. She uses HMAC and appends HMACHMAC(k, file-namenfile -contentn) to each file n. She updates this value for every change she makes to each file. Explain how an attacker (Eve) can make the following changes without being detected by Alice 1. Content of one of Alice’s files has changed 2. One of Alice’s file has been deleted 3. A new file
OR
OR
