Show pictures for steps 2, 5, 7 and 9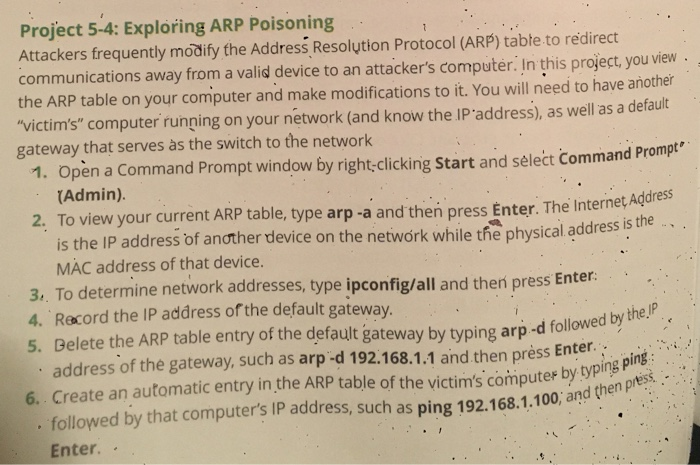
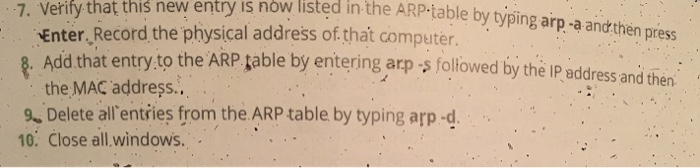
what is the result of the project once all steps have beencompleted?Project 5-4: Exploring ARP Poisoning Attackers frequently modify the Address Resolution Protocol (ARP) tabte to redirect communications away from a valid device to an attacker’s computer. In this project, you view the ARP table on your
OR
OR
